Cyber Security Threats, Trends and Best Practices For Businesses
In the ever-evolving digital landscape of today, businesses, regardless of their size, face constant and escalating concerns regarding cyber threats. Recent research conducted by Fortinet reveals that a staggering 70% of organizations encountered a data breach within the past year alone.
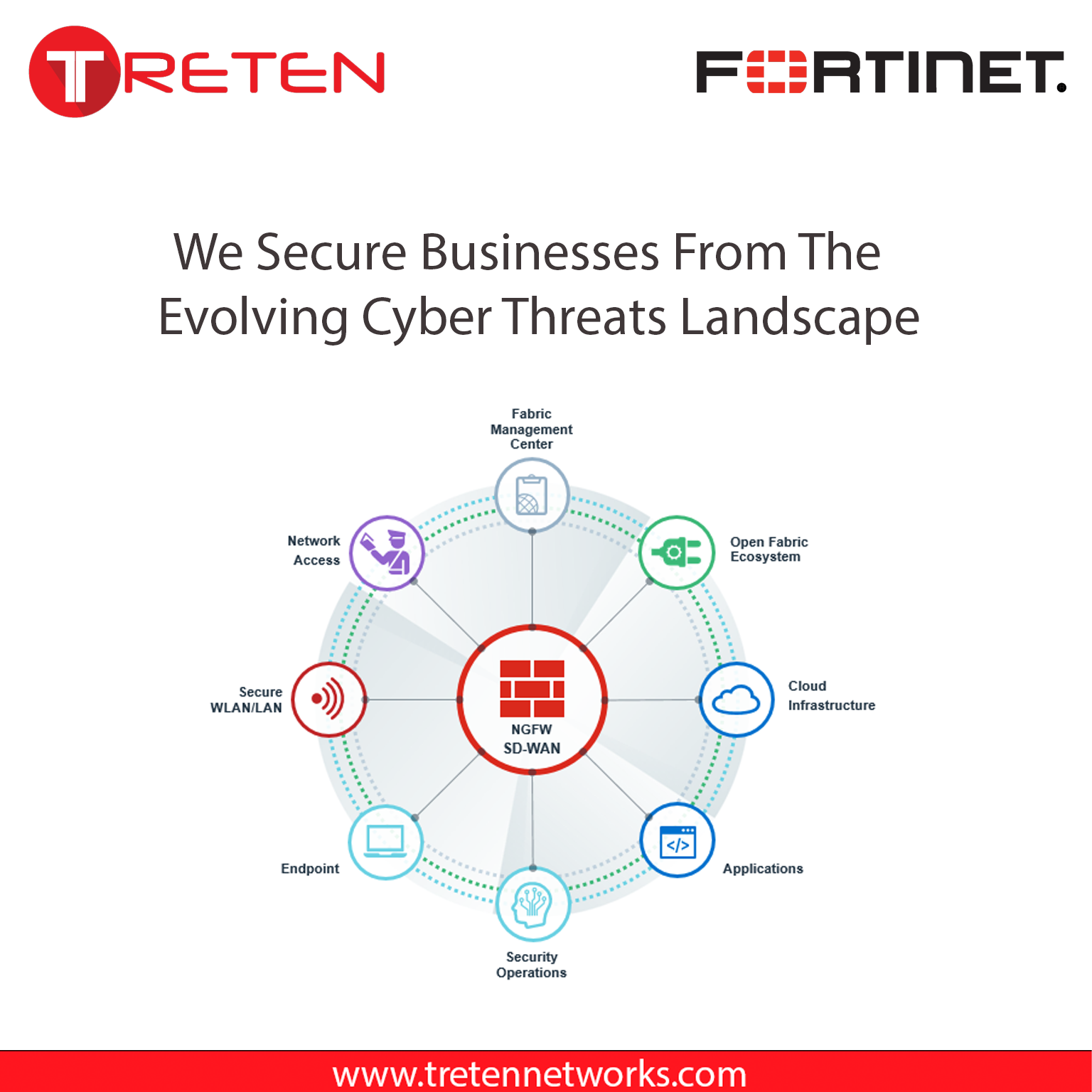
To address this pressing issue and aid organizations in safeguarding themselves against such threats, Treten Networks has formed a strategic partnership with Fortinet, offering a holistic suite of security solutions. These comprehensive solutions encompass:
- Fortinet FortiGate firewalls: These firewalls provide extensive protection against a broad spectrum of cyber threats, including malware, ransomware, and DDoS attacks.
- Fortinet FortiWeb web application firewalls: These firewalls shield web applications from attacks, effectively mitigating data breaches and other security incidents.
- Fortinet FortiAnalyzer network security appliances: These appliances offer centralized visibility and control over network traffic, facilitating the identification and response to security threats.
Alongside these security solutions, Treten Networks provides a range of training and support services to assist organizations in the efficient implementation and maintenance of their security measures.
Trends in Cyber Threats
The cyber danger landscape is always advancing, and organizations ought to be prepared to face new and developing dangers. Here are some of the foremost vital cyber threat trends to be careful for in 2023:
- Ransomware: Ransomware could be a sort of malware that encrypts a victim’s records and requests a ransom payment in order to decode them. Ransomware attacks have gotten to be progressively predominant in recent years, and the ransom demands have moreover expanded. In a few cases, ransom requests have come into millions of dollars.
- Phishing: Phishing may be a sort of social building attack in which attackers send emails or text messages that show up to be from a genuine source, such as a bank or credit card company. These messages frequently contain links that divert victims to false websites that look like the genuine site. Once the victim enters individual data on the fraudulent site, the attacker can steal that data.
- Data breaches: Data breaches are another major cyber risk. A data breach happens when an attacker picks up unauthorized access to a framework and steals delicate information. This information could include client personally identifiable data (PII), money related records, or intellectual property. Data breaches can have a devastating effect on businesses, both financially and reputationally.
- Supply chain attacks: As organizations progressively depend on third-party vendors for critical administrations, they become more helpless to supply chain attacks. In a supply chain attack, the attacker targets a third-party seller in order to pick up unauthorized access to the organization’s frameworks. Once the attacker has gained access to the organization’s frameworks, they can take data, install malware, or disturb operations.
- IoT attacks: The expansion of Internet of Things (IoT) devices has created new openings for attackers. IoT devices are regularly ineffectively secured, making them simple targets for attackers. Attackers can abuse IoT devices to dispatch denial-of-service attacks, take information, or even assume remote control over the devices.
Best Practices for Cybersecurity
Organizations can adopt several best practices to bolster their cybersecurity stance. Some of the most crucial measures include:
- Implementing a comprehensive security strategy: An effective security strategy should encompass preventive, detective, and corrective measures.
- Ensuring software updates: Regular software updates often include security patches that safeguard systems against known vulnerabilities.
- Providing security training for employees: Educating employees about security best practices, such as identifying phishing emails and creating robust passwords, is essential.
- Establishing an incident response plan: A well-defined plan outlining steps for identifying, containing, and recovering from cyberattacks is vital.
By adhering to these best practices, organizations can fortify their defenses against the prevailing cyber threats.
Fortinet and Treten Networks:
A Cybersecurity Partnership Treten Networks and Fortinet share a collective commitment to assisting organizations in defending against cyber threats. Through our collaboration, we strive to create a safer world.
Fortinet, renowned globally for its cybersecurity solutions, and Treten Networks, a prominent provider of security consulting and services, combine Fortinet’s profound security expertise with Treten
Networks’ demonstrated track record in delivering effective security solutions. Together, we empower organizations of all sizes to:
- Gain comprehensive understanding of the cyber threats they face.
- Implement robust security solutions tailored to their needs.
- Equip employees with the necessary knowledge and skills through security training.
- Respond effectively to cyberattacks.
Given the ever-evolving nature of the cyber threat landscape, organizations must stay prepared to handle modern and developing dangers. By following to the best practices laid out in this Cyber Security Threats, Trends and Best Practices For Businesses article, organizations can improve their cyber security posture and defend themselves against the diverse dangers they encounter.
Here are extra recommendations for organizations looking for to support their cyber security posture:
- Utilize a Security Information and Event Management (SIEM) arrangement: A SIEM solution empowers you to accumulate and analyze security logs from across your organization, making a difference identifying potential threats and take proactive measures to mitigate them.
- Implement a zero-trust security model: Embracing a zero-trust security model assumes that no client or device is naturally trusted, even when inside your network. This approach reduces the attack surface and makes it more challenging for attackers to pick up unauthorized access to your frameworks.
- Invest in security training for employees: Recognize that employees frequently serve as the weakest link within the security chain. Giving comprehensive security training helps them understand the dangers posed by cyber threats and equips them with the knowledge to protect themselves.
- Develop a robust incident response plan: Cyberattacks can happen at any time. Having a well-defined plan in place to reply to such occurrences empowers organizations to minimize harm and recover quickly.
By following these suggestions, organizations can elevate their cyber security posture and effectively mitigate the dangers they confront.
If your organization is located in Lagos, Abuja, Nigeria, UAE, the United Kingdom, Canada, Ghana, Cameroon, Rwanda, Ethiopia, or the British Virgin Islands, we invite you to reach out to Treten Networks today. We would be delighted to discuss your specific needs and collaborate in developing a comprehensive cyber security plan.