Understanding the Basics: Cyber Security 101 In the present hyper-connected world, the requirement for cyber security has risen above the domain of tech specialists and become a key piece of our day to day exis...
The Ultimate Guide to Network Access Control: Enhancing Security and Streamlining Efficiency In today’s quick moving digital scene, guaranteeing network security is a major concern. As cyber dangers grow ...
10 Foolproof Ways to Spot and Avoid Phishing Scams – Protect Yourself Online Recognizing phishing scams is fundamental in the present digital age to shield yourself and your sensitive data from cybercrimi...
Securing the Internet of Things: Safeguarding Your Connected Devices with IoT Security The Internet of Things (IoT) is decisively reshaping our day to day routines and expert conditions. With billions of interc...
The future of IT Cybersecurity: Securing Your Digital Assets from Modern Threats. In a progressively digital world, the looming specter of cyberattacks poses a developing threat. Cybercriminals’ tactics a...
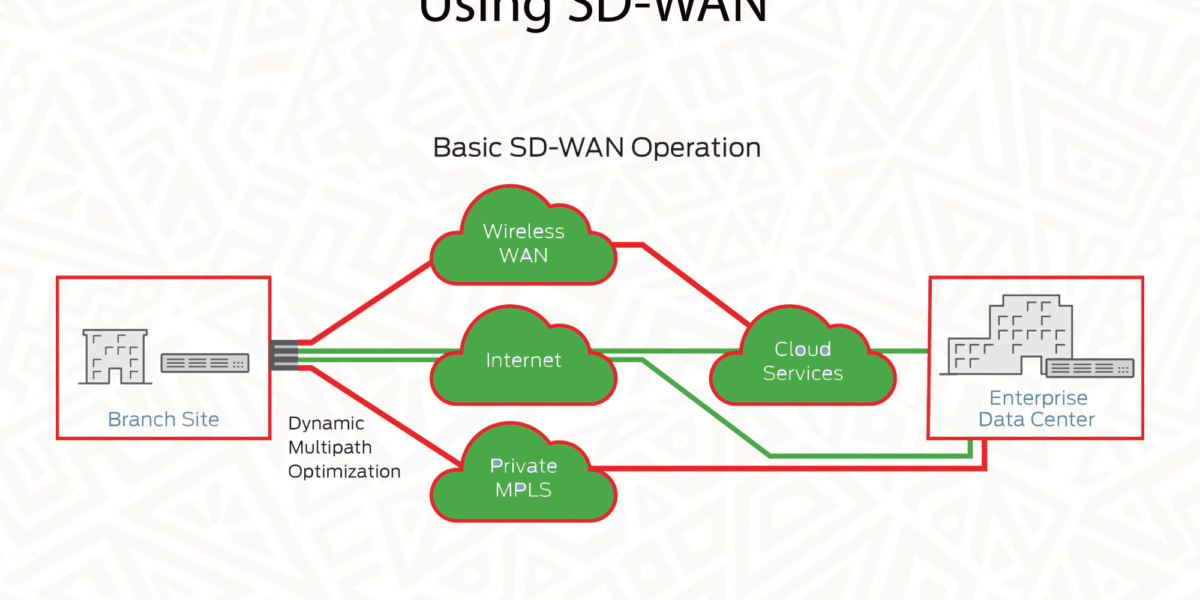
SD-WAN: How To Improve Your Business Network In the dynamic landscape of evolving digital ecosystem, businesses are embracing technological innovation to unlock new avenues of growth. As the cloud becomes the b...
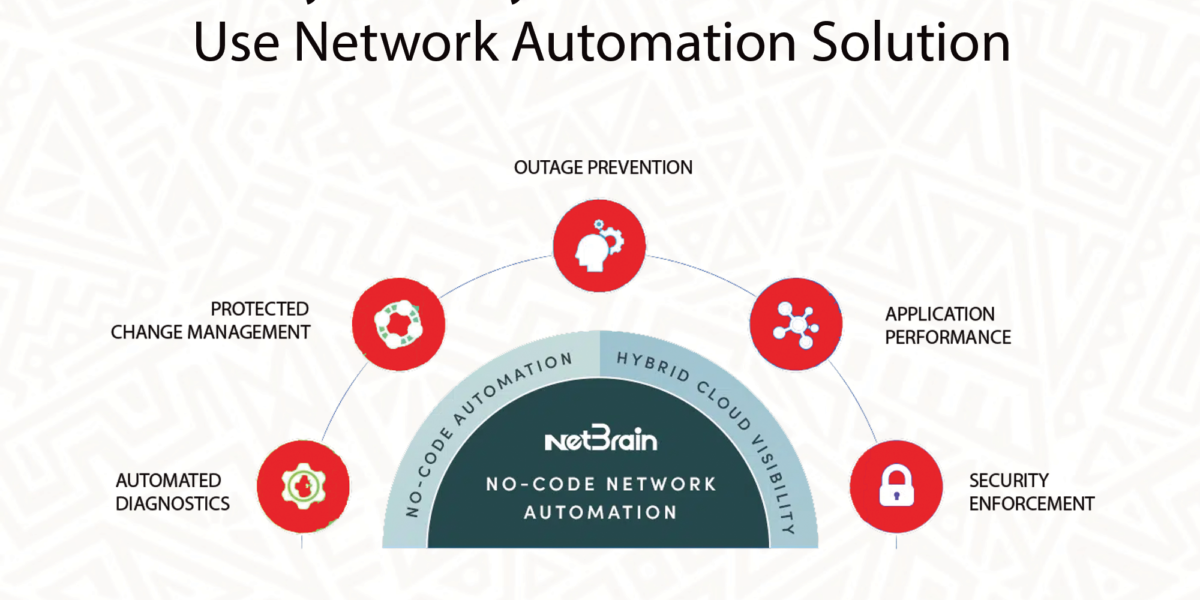
How to Automate Your Network and Improve Your Business’s Efficiency In an era characterized by rapid technological advancements, businesses are constantly grappling with the need to adapt swiftly to chang...
Protect Your Business Data with Cloud Security and Compliance In today’s rapid digital landscape, businesses are quickly grasping cloud-based applications and services to remain competitive and agile. Be ...
How to Improve Your Network Security with NGFW Technology In today’s ever-changing threat landscape, businesses confront a steady fight to defend their sensitive information and critical assets from tenac...
Enhancing Business Efficiency with Enterprise Storage Solutions In today’s data-driven business landscape, effectively overseeing and storing information is pivotal for success. However, traditional stora...