The Ultimate Guide to Network Access Control: Enhancing Security and Streamlining Efficiency In today’s quick moving digital scene, guaranteeing network security is a major concern. As cyber dangers grow ...
10 Foolproof Ways to Spot and Avoid Phishing Scams – Protect Yourself Online Recognizing phishing scams is fundamental in the present digital age to shield yourself and your sensitive data from cybercrimi...
Securing the Internet of Things: Safeguarding Your Connected Devices with IoT Security The Internet of Things (IoT) is decisively reshaping our day to day routines and expert conditions. With billions of interc...
Unleashing the Power of Network Performance Optimization: In our fast-paced advanced era, network performance has gotten to be more critical than ever. Businesses, notwithstanding of their size, intensely depen...
Understanding the New Threat to Security: The Rise of Cyber Espionage In today’s interconnected world, cyber espionage has emerged as a formidable threat, posing a grave risk to entities of all sizes, whe...
Exploring Cyber Security Salaries in Nigeria: Insights from Treten Networks Navigating the world of cyber security careers and their corresponding salaries can be quite a complex task, especially in a region li...
The future of IT Cybersecurity: Securing Your Digital Assets from Modern Threats. In a progressively digital world, the looming specter of cyberattacks poses a developing threat. Cybercriminals’ tactics a...
Unlocking the Power of Application Security: Safeguarding Your Digital Assets with Proven Strategies
Unlocking the Power of Application Security: Safeguarding Your Digital Assets with Proven Strategies. In today’s digital era, both our businesses and personal lives heavily rely on digital resources. Thes...
The approach of the digital period has introduced in a huge number of advantages, extending from comfort and improved communication to uncommon access to data. Be that as it may, in couple with these benefits, ...
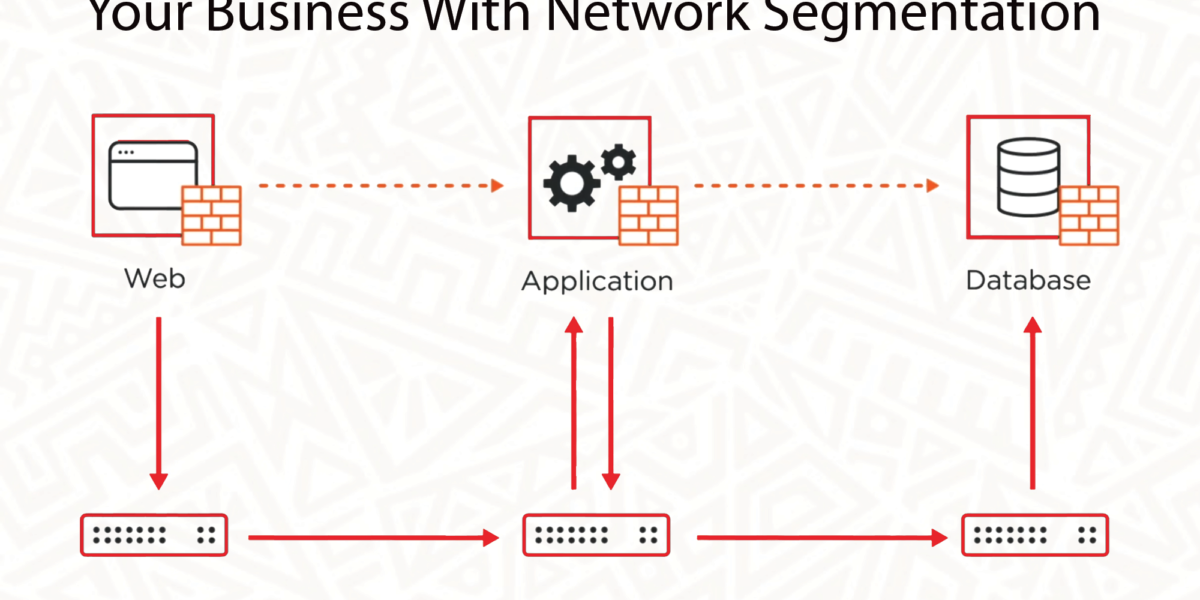
The Ultimate Guide to Network Segmentation: Enhancing Security and Performance. In the digital age, where cyber threats are constantly evolving, safeguarding sensitive data and maintaining the integrity of a ne...